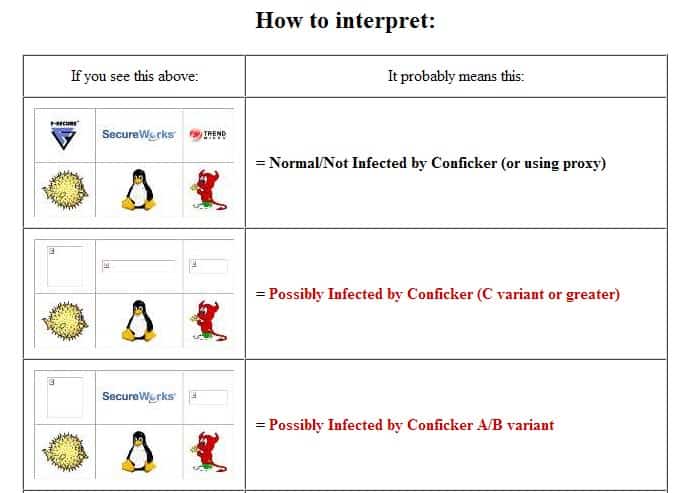
Brilliant Tips About How To Detect Conflicker C

The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445.
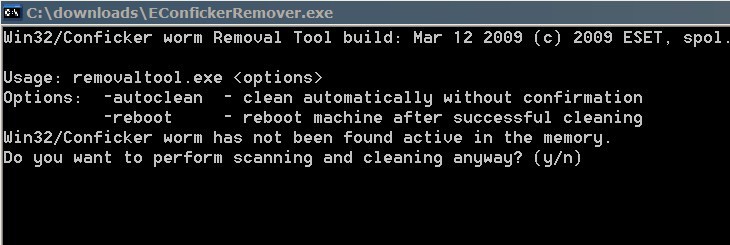
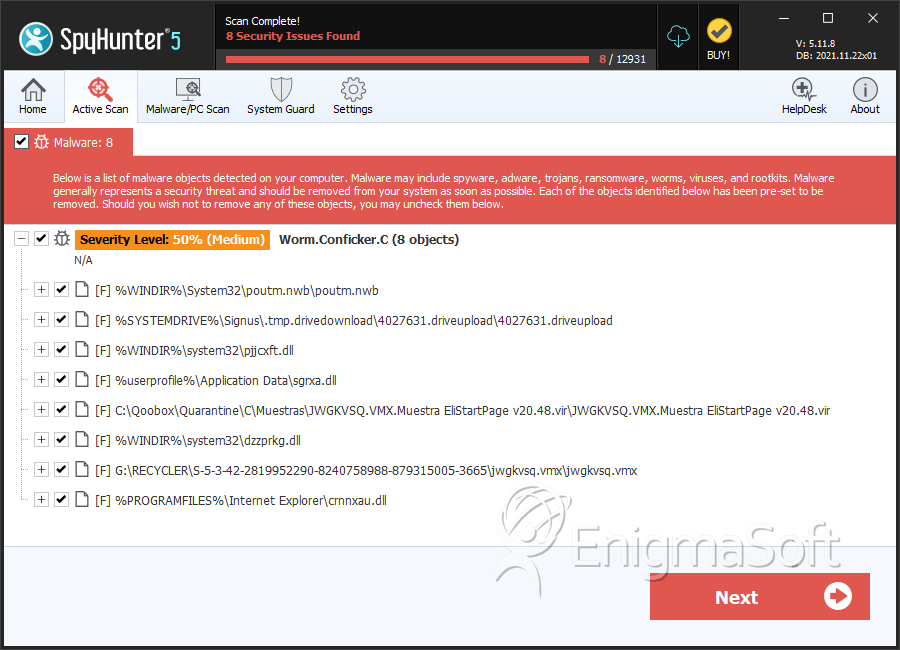
How to detect conflicker c. National transportation safety board officials speak during a 2019 news conference. You might need to get a tool specifically for the conflicker worm and might need to download it from a computer that is not infected. Once conficker.c malware settles on the operating system, it will add a specific file to the removable drive to the local drives.
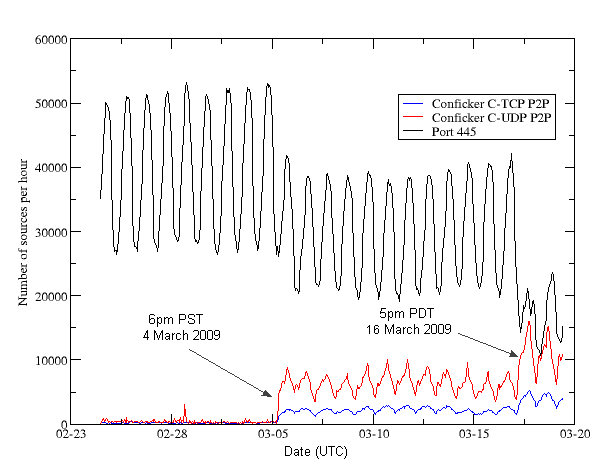
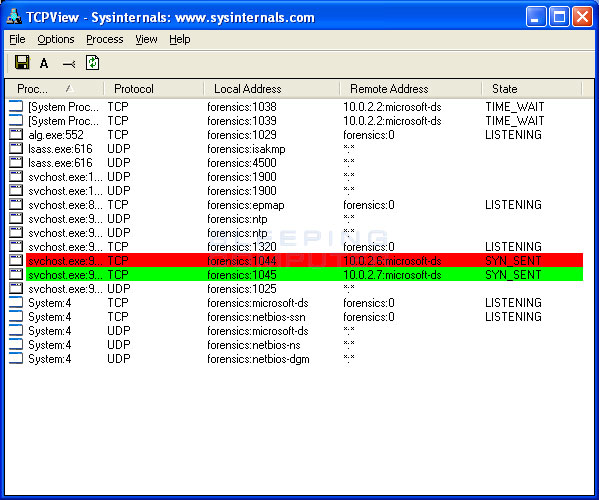
You may check for conficker.c traffic on a particular side of the flow, or for both sides: 5 hours agocalifornia crash that killed 9 spurs call for new cars to detect drunk drivers. Until recently, there were only two ways to detect conficker, which included monitoring outbound network connections for individual computers, or target scanning each.
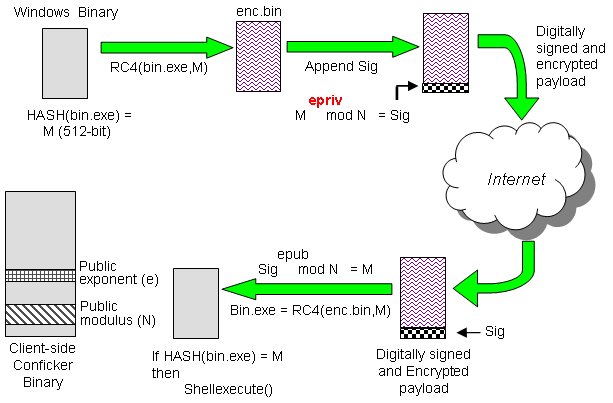
Then the dialogue box emerges asking to “open. Checks if a host is infected with conficker.c or higher, based on conficker's peer to peer communication. Check the computer with panda activescan, panda security's free, online scanner, which will quickly detect any possible viruses.
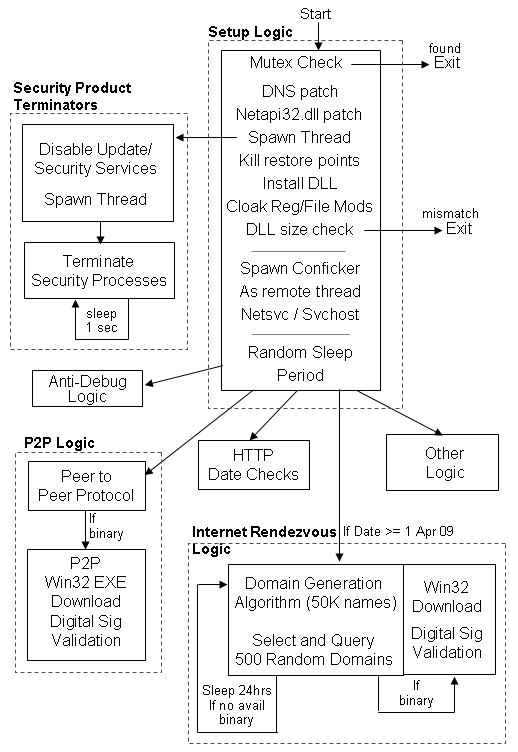
Certain microsoft windows services such as automatic updates, background intelligent. But security experts appeared correct in their. Security watchers at mcafee say that conficker is trying to communicate with master computers but isn't getting through.
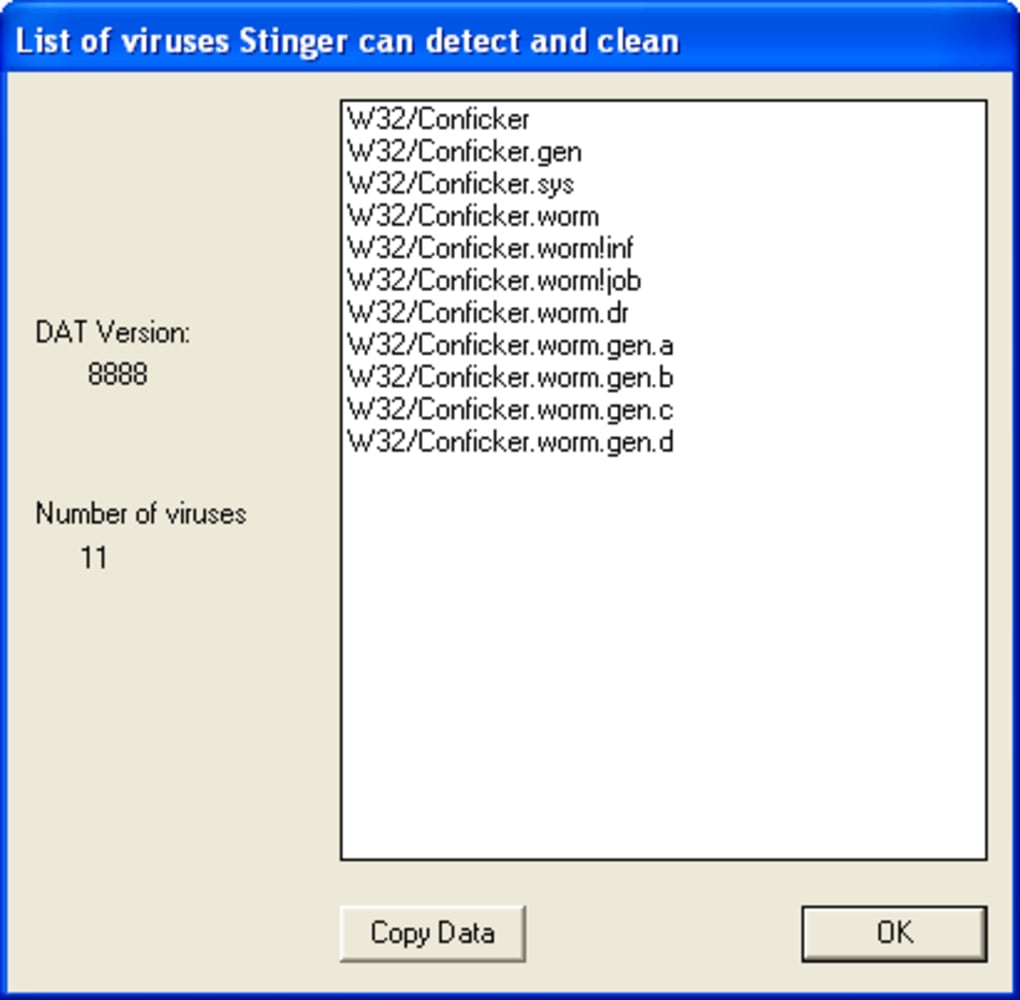
(opens in new tab) from the microsoft malware protection center. Read microsoft's information on how to remove conflicker. Symptoms of a conficker infection include:
Microsoft security software detects and removes this threat. When conficker.c or higher infects a system, it opens four ports: Run the malicious software removal tool.
If panda antivirus or panda. This family of worms can disable several important windows services and security products.



/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)